OPC Tunneller and OPC Bridging
Enabling OPC Classic/OPC UA interoperability; facilitating cross-network communications
Why is the OPC Tunneller Required for Industries?
A tunneller eliminates the problems associated with DCOM while connecting OPC clients to servers. The OPC bridging tunneller is a combination of an in-built OPC wrapper and a proxy. A brief explanation on their working is given below.
OPC UA Proxy

OPC UA Wrapper

OPC UA Tunneller
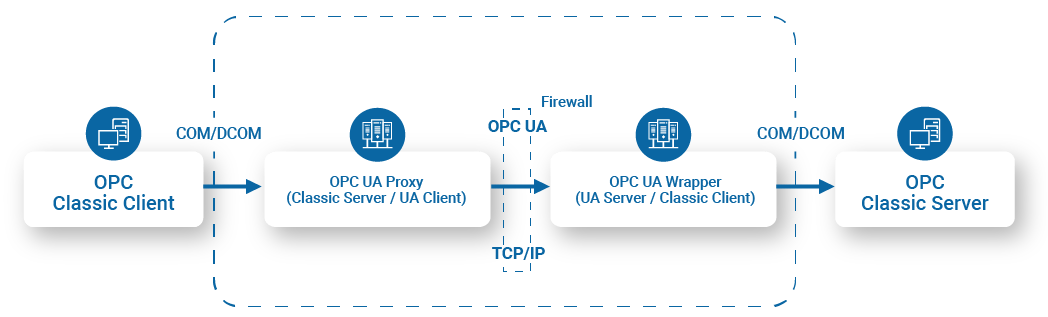
- Connect OPC Classic client to OPC Classic server across the firewall by-passing DCOM communication as shown in Figure 3 above.
- Connect OPC Classic client to OPC UA server using the OPC UA Proxy as shown in Figure 1.
- Connect UA client to OPC Classic server using the OPC UA Wrapper as shown in Figure 2.
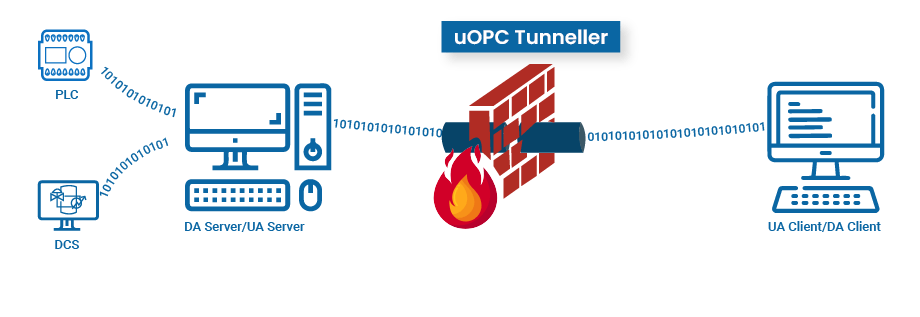
OPC Tunneller Product Provided by Utthunga
The two uOPC Tunneller components communicate with one another via OPC UA. IT engineers managing the network infrastructure will add the port number and IP addresses of the servers and clients details in the firewall settings of the router as part of the port forwarding mechanism. Additional DCOM configuration is not required and Windows firewall configuration is limited to allowing access to the port being used by the uOPC Tunneller components on the respective machines.
uOPC® Tunneller from Utthunga Suite has the following Features
- Supports OPC Classic, OPC DA (v1.0, v2.0 and v3.0), OPC AE v1.0, OPC HDA v1.0, OPC UA v1.02
- Protocols Supported: OPC Client drivers for OPC UA, DA, AE & HDA
- Supports single instance for uOPC® Tunneller Client (also called as Proxy Server) when it connects to one or more OPC UA Tunneller Server(s)
- Supports dynamic runtime browse of new tags injection in OPC Classic server(s)
- Supports bulk tags per subscription
- Allows automatic reconnect
- Provides support for tracking status of underlying OPC Server(s)
- Security is provided via data signing & encryption along with user authentication & authorization

Software Platform Requirement
- Target OS: Windows 7 (32Bit/64Bit), Windows 8/8.1 (32Bit/64Bit), Windows 10 (32 bit/64 bit), Windows Server 2008 RS2 (32Bit/64Bit), Windows Server 2012 RS2

Hardware Platform Requirement
- CPU – Intel (i3, i5, i7) family or its AMD equivalent.
- RAM – 8 GB or above.
- HDD – 250 GB or above.
Why OPC Tunneller from Utthunga?
- Overcome OPC timeout issues and network disconnections caused by DCOM setup
- Eliminate DCOM usage for OPC Classic connectivity and data transfer through firewalls
- Reduce costs by eliminating rip-and-replace of OPC Classic assets
- Reduce network bandwidth utilization and increases throughput
- Provide secure, encrypted and authentic communication between OPC clients and servers
- Leverage diagnostic tools for easy troubleshooting
